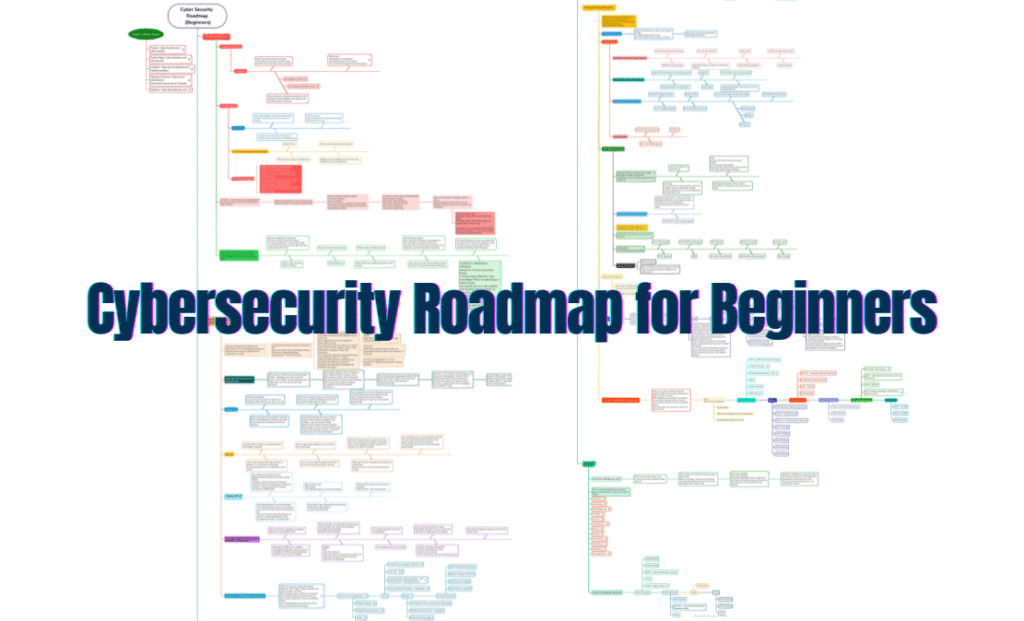
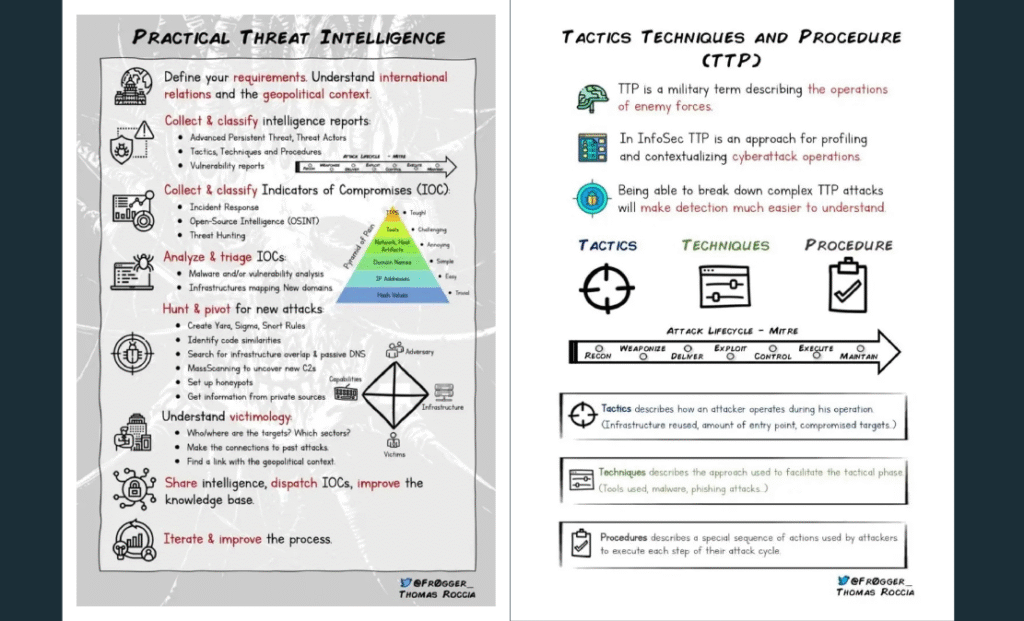
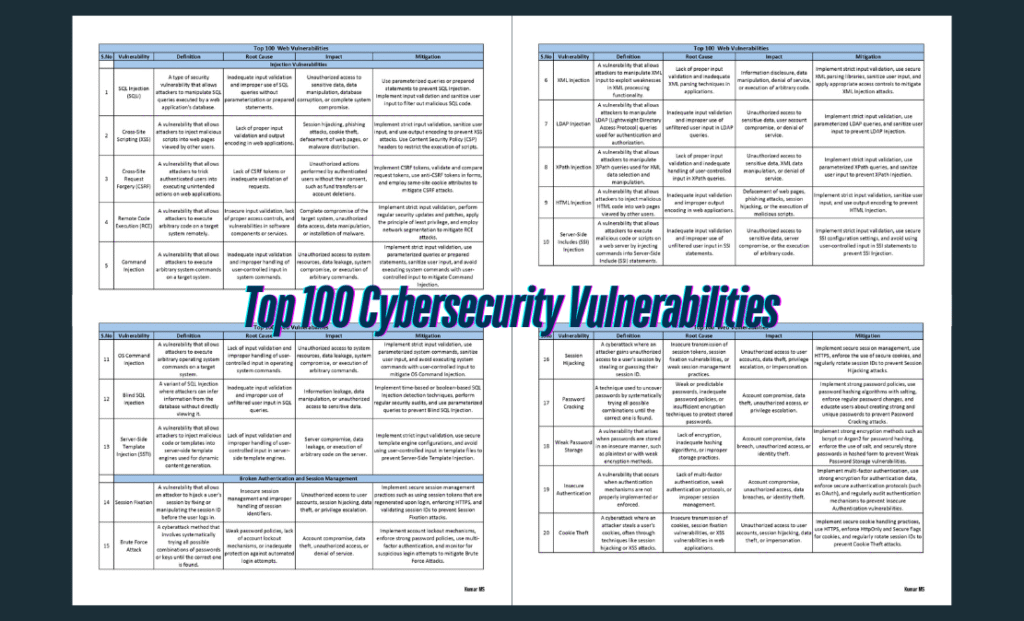
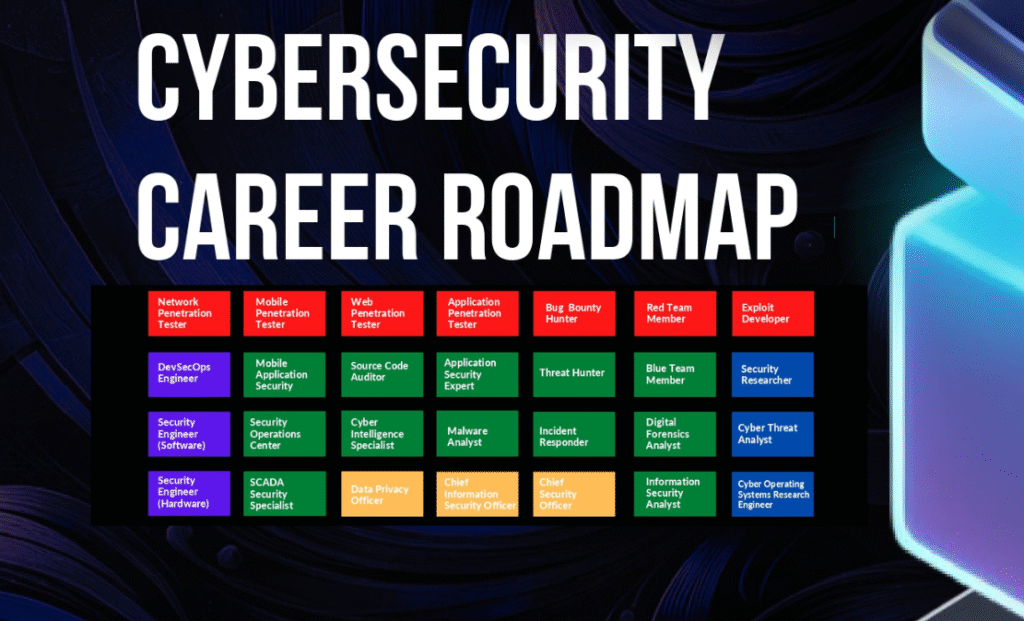
Cybersecurity Roadmap for Beginners: A Comprehensive PDF Guide
In the rapidly evolving digital age, cybersecurity has become an indispensable component of our online presence. As technology continues to advance, so do the threats that exploit vulnerabilities in our digital systems. For beginners eager to step into the world of cybersecurity, having a well-structured roadmap is essential. This blog post introduces you to a […]
Cybersecurity Roadmap for Beginners: A Comprehensive PDF Guide Read More »